Digital twins have revolutionized how we manage and interact with physical systems, yet they also bring new security demands. The virtual representation of a physical object or system poses unique challenges that require smart, proactive defenses.
We at Newroom Connect know that an ounce of prevention is worth a pound of cure, especially when it comes to guarding the digital counterpart of our critical systems. This post will outline actionable strategies to reinforce the safety of your digital twin against emerging security threats.
Securing Your Digital Twin
When digital twin technology is embraced, it brings along an expanded attack surface. Essentially, every sensor, device, or system connected to a digital twin is a potential entry point for security threats. Rather than deterring their use, we should double down on securing these innovative assets.
IoT devices bolster digital twins but are notorious for their vulnerabilities. They are often the weakest links due to inconsistent updates and lax security standards. Legacy systems further compound these risks; they weren’t designed for the interconnectedness of modern technology, making them easy prey for cyberattacks.
Continuous monitoring for unusual activity is essential. Real-time anomaly detection can act as an early alert system, flagging deviations that could indicate a breach. Quick detection coupled with rapid response measures can mitigate potential damage.
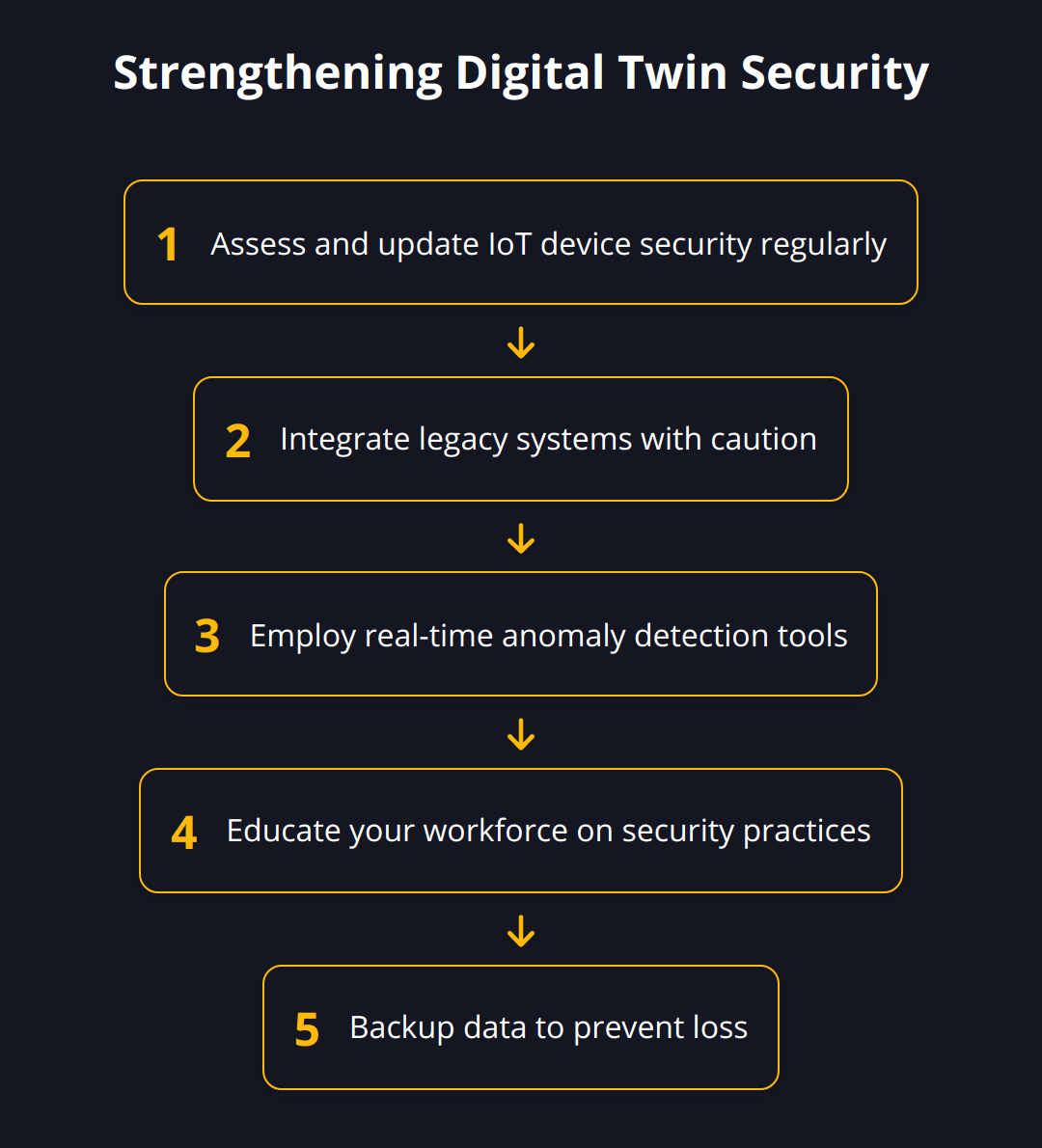
Here’s how to tighten the digital defenses around your digital twin:
-
Assess and Update: Regularly evaluate the security of your IoT devices and update them. Outdated software is a leading cause of security breaches.
-
Integrate Legacy Systems Cautiously: When tethering legacy systems to your digital twin, ensure they don’t introduce vulnerabilities.
-
Employ Anomaly Detection Tools: Use advanced tools that can identify irregular patterns in real-time. Tools such as digital twin development platforms can provide frameworks to integrate such measures.
-
Educate Your Workforce: Ensure your employees are aware of the potential risks and are trained to recognize and report anomalies.
-
Backup Your Data: Regular backups can reduce the harm of data manipulation or loss in the event of a cyberattack.
A proactive stance is imperative to secure your digital twin against the myriad of security threats it faces. Implement these practices, stay informed about emerging risks, and you’ll position your digital assets to withstand the evolving landscape of cyber threats.
How to Enhance Digital Twin Security
Protecting your digital twin from cyber threats calls for stringent, forward-thinking strategies that adapt alongside the ever-changing cyber landscape. Building a robust defense system for your virtual assets is not just wise; it’s imperative for operational continuity and maintaining trust with stakeholders.
Including Cybersecurity Specialists Early On
Involve cybersecurity experts right from the planning phase of your digital twin initiative. Their insights will be invaluable in identifying potential vulnerabilities and recommending best practices tailored to your setup. Cybersecurity professionals can guide the selection of secure IoT devices and establish protocols to integrate legacy systems safely. It’s not just the right move—it’s a strategic necessity.
Adopting Zero Trust for Your Virtual Counterpart
Zero trust is not just a buzzword; it’s an advanced approach to security that assumes no entity within or outside the network is automatically trustworthy. Insisting on continuous verification for all accessing or moving within your digital twin’s network is not paranoia—it’s smart security. Apply zero-trust principles vigorously to minimize the chances of unauthorized access and subsequent breaches.
Implementing Secure Network Design
Your digital twin demands a network design that’s as robust as it is resilient. Secure network segmentation is a method where the network is split into multiple zones, with strict controls on traffic between them. Segmentation not only limits an attacker’s lateral movement within your networks but also provides fine-grained control over who accesses what. Engineer your network with distinct layers of security, and you’ll have a defense that mirrors the sophistication of your digital twin.
-
Stay Vigilant and Update: Cyber threats evolve, and so must your security practices. Regularly updating and patching your systems is the first line of defense.
-
Strict Access Controls: Limit access to your digital twin by implementing stringent permission controls—nothing less than tight is acceptable.
-
Monitor, Monitor, Monitor: Keeping an ever-watchful eye on your systems through monitoring tools is a game-changer in spotting threats early.

In conclusion, the stakes are high, and so must be the level of security around your digital twin. Treat it as you would any critical infrastructure—because that’s precisely what it is. By implementing these practices, you strengthen your fortifications against the relentless tide of cyber threats. Be vigilant, be proactive, and you’ll navigate the digital twin’s security challenges with confidence.
Remember, the next chapter will build upon these foundations, exploring advanced tactics to further empower your digital twin against the sophisticated threats of the digital age.
Enhancing Security with Digital Twins
Digital Twins serve as more than a bridge between the physical and digital worlds. They are powerful tools in the war against cyber threats, offering the ability to detect and respond to issues before they escalate. With digital twins, we can turn the tables on cyber attackers and use these assets for thorough vulnerability assessments and enhanced operational technology protection.
Digital Twins as an Early-warning System
Imagine having a sentinel that never sleeps, constantly scanning for danger. That’s the role digital twins can play in cybersecurity. By mirroring physical systems, digital twins can help detect anomalies signifying potential security incidents. Here are practical steps to establish digital twins as a linchpin of your threat defense strategy:
-
Monitor network traffic and user behavior to detect early signs of compromise.
-
Set up a digital twin to replicate critical system functions for continuous operational oversight.
-
Implement alerts to flag deviations from normal operation, signaling potential security breaches.
Digital twins’ real-time data flow allows you to spot discrepancies instantly, providing that crucial window to brace for impact or neutralize a threat.
Utilizing Digital Twins for Security Testing and Simulation
One potent application of digital twins is creating a sandbox environment to test security measures without risking the actual system. Here’s how to make the most of this feature:
-
Run penetration tests and simulate cyber-attacks within the digital twin environment.
-
Analyze the outcomes of those tests to patch vulnerabilities in the physical systems.
-
Apply the insights gained from simulations to enhance the security posture of your real-world assets.
By stress-testing your systems in a controlled virtual setting, you can uncover and address weaknesses before attackers exploit them.
Protecting Operational Technology Assets with Digital Twin Insights
Operational technology systems are often the backbone of business operations but can be exposed to cyber risks when connected to digital twins. To safeguard these assets:
-
Use your digital twin’s data to identify abnormal patterns in machine operation that might suggest a security issue.
-
Conduct predictive maintenance by analyzing digital twin data, which can help prevent system malfunctions that could lead to vulnerabilities.
-
Integrate cybersecurity features into the digital twin design, ensuring a layer of protection is built around these critical systems.
Employing digital twins not only enhances your operational insight but bolsters your defense against cyber threats targeting these crucial technology assets.
To further emphasize the importance of digital twin technology in cybersecurity, consider these points:
-
Proactive Monitoring: Leveraging your digital twin for active monitoring can significantly reduce the time to detect and respond to security incidents.
-
Simulation Advantages: Regular security testing against your digital twin can prevent as much as 70% of potential breaches, according to industry research.

- OT Protections: Operational technology systems connected to digital twins are better shielded from cyberthreats when predictive analytics are used to preemptively resolve security gaps.
Embracing digital twins for these purposes equips you with advanced capabilities to safeguard your systems. This is not future talk; it’s an immediate, actionable strategy that provides a competitive edge in cybersecurity.
The upcoming chapter will delve into the nitty-gritty details of creating a resilient security infrastructure melding digital twins with the latest cyber defense tactics. Here, we’ll discuss securing not only the twin but also creating a digital fortress for your enterprise’s entire digital presence. Stay proactive and ready to adapt, the digital landscape waits for no one.
Continuous Digital Twin Security Tactics
Ongoing vigilance is key to protecting your digital twin technology. In this chapter, we focus on the concrete steps required to ensure that your digital twin remains secure against the ever-evolving nature of cyber threats. Sharing knowledge across departments, leveraging the latest in cybersecurity, and regular assessments all form the cornerstone of a strong defense strategy.
Regular Security Assessment and Threat Modeling
Casting a critical eye on your security measures consistently is fundamental. What may have been a solid defense yesterday might not stand up to today’s sophisticated cyber threats. Building a routine of exhaustive threat modeling and security assessment is just good operational sense.
-
Perform comprehensive security audits every quarter to uncover potential vulnerabilities.
-
Engage in threat modeling to predict and prepare for potential attack scenarios specific to your digital twin infrastructure.
-
Update your risk assessments to reflect new information and adjust protections as necessary.
A continuous loop of evaluation and modification fortifies your security posture and prepares you for the unexpected.
Up-to-the-Minute Cybersecurity Innovations
The digital security world never stands still, and neither should your security strategy. Innovations can come from research breakthroughs, technological advancements, or freshly devised best practices.
-
Subscribe to leading cybersecurity research journals or platforms for the latest findings.
-
Attend industry webinars about digital twin security and participate in relevant discussions.
-
Utilize cybersecurity platforms that focus on digital twin safety.
Tapping into these resources ensures that your defenses are not just current but cutting edge.
Fostering Interdepartmental Collaboration
No system is secure in silos. Protection against threats to your digital twin requires unified efforts across all departments. The involvement of IT, operations, and even HR is crucial for comprehensive security.
-
Host regular cross-functional meetings to ensure all departments understand the digital twin’s role and associated risks.
-
Develop company-wide security protocols so that everyone is on the same page when it comes to responding to threats.
-
Create feedback loops so that any security concerns or insights can be reported and acted upon swiftly.
Building a culture that values security as a collective responsibility leads to shared vigilance and more robust protection.
Key Takeaways:
-
Regular security check-ups and adapting threat models are not optional; they’re a necessity.
-
Staying well-informed on security advancements is pivotal.
-
Collaborative efforts across departments significantly strengthen your digital twin’s security.
Rather than simply reacting to threats, the measures outlined here are about fostering a proactive security culture around your digital twin. This proactive stance is not just about safeguarding a digital asset; it’s about protecting your organization’s operational backbone – a responsibility that warrants top-tier strategic thinking and execution.
Securing a digital twin is a dynamic challenge, requiring ongoing attention and a willingness to adapt quickly. With robust security protocols, regular assessments, and an organizational commitment to cybersecurity, you’re equipped to face the fluid landscape of digital threats head-on. The strategies discussed set the stage for more advanced protective measures, as security doesn’t end here—it evolves.
Final Thoughts
As we conclude our exploration of digital twin security, it’s evident that the proactive and multi-layered strategies we’ve discussed are central to any robust defense. The convergence of digital and physical worlds through digital twins necessitates a vigilant and resilient approach to safeguarding these assets. Reflective of Newroom Connect’s expertise in creating secured virtual environments, the following recapitulates our salient points on securing digital twins.

Protecting digital twins is not a one-off task but an ongoing process that demands continuous attention and adaptation to new threats. By employing a security-centric mindset from the outset, conducting regular assessments, and fostering a culture of interdepartmental collaboration, businesses can build robust defenses around their digital twins.
Key Strategies Recap:
-
Vigilantly update and patch systems as part of your routine.
-
Strict permission controls and access management are essential for limiting risks.
-
Ongoing monitoring to detect threats swiftly.
These actions are foundational, yet they must be accompanied by an unwavering commitment to continuous improvement. The cybersecurity landscape is ever-changing and our defenses must evolve accordingly to address new vulnerabilities and attack vectors that emerge.
The Necessity for Continuous Improvement:
-
Embrace advancements in cybersecurity measures.
-
Integrate feedback loops for timely threat response.
-
Adapt security protocols to meet the changing digital environment.
Continuous improvement in digital twin security also involves embracing robust security frameworks during deployment. Relying on advanced platforms that embed security from the ground up is essential to mitigating threats before they take root.
Adoption of Security Frameworks:
-
Include cybersecurity specialists in the digital twin design phase.
-
Implement security frameworks that feature cutting-edge protection measures.
-
Review and refine cybersecurity frameworks regularly.
At Newroom Connect, we understand the intricate nature of the relationship between digital and physical assets. Our offerings, from virtual trade fairs to e-learning platforms, are designed to provide both exceptional user experiences and high-caliber security. We are dedicated to empowering our clients with the tools and knowledge needed to safeguard their virtual environments effectively.
Securing digital twins is ultimately about safeguarding your business’s future. It ensures the integrity of your operations, the trust of your stakeholders, and the resilience of your enterprise. By adopting these robust security strategies and committing to continuous improvement, your organization can confidently navigate the path forward in the digital arena.


